SQL injection (SQLi) is a serious security vulnerability that can allow attackers to manipulate a website’s database. In this blog post, we will explore what SQL injection is, how attackers exploit it, and most importantly, how you can protect your website from such attacks. We’ll keep things simple and engaging, so even a fifth-grader could understand!
What is SQL Injection?
SQL injection is when an attacker inserts or “injects” malicious SQL code into a web application’s input fields. This can happen in places like login forms, search boxes, or any field that interacts with a database. If the application does not properly handle this input, the attacker can gain unauthorized access to sensitive data or even take control of the entire database.
How Would an Attacker Use SQL Injection?
Imagine a website that asks for your username and password. The application might run a SQL query like this:
SELECT * FROM users WHERE username = 'user' AND password = 'pass';
If an attacker inputs something like user' OR '1'='1, the query becomes:
SELECT * FROM users WHERE username = 'user' AND password = 'password' OR '1'='1';
This trick allows the attacker to bypass authentication and potentially access sensitive data.
Basics of SQL Injection
Common Methods Attackers Use
- In-Band SQL Injection: This is the most straightforward method where attackers use the same channel to inject and retrieve data.
- Error-Based SQL Injection: Attackers manipulate queries to generate errors that reveal information about the database.
- Union-Based SQL Injection: Attackers use the UNION operator to combine results from multiple queries.
- Out-of-Band SQL Injection: This method relies on the database’s ability to make HTTP requests. It’s less common but can be very effective.
How Can SQL Injection Be Prevented?
Preventing SQL injection is crucial for maintaining the security of your website. Here are some effective methods:
1. Use Parameterized Queries
Parameterized queries ensure that user input is treated as data, not executable code. For example, instead of constructing a query like this:
sql = "SELECT * FROM users WHERE username = '" + username + "'";
Use prepared statements:
stmt = connection.prepareStatement("SELECT * FROM users WHERE username = ?");
stmt.setString(1, username);
2. Validate Input
Always validate user input. Check for expected formats and reject anything suspicious. For example, if you expect a number, ensure that the input contains only digits.
3. Implement Proper Error Handling
Don’t expose database errors to users. Instead, log errors internally and show generic error messages to users. This prevents attackers from gaining insights into your database structure.
4. Limit Database Permissions
Restrict what each database user can do. For example, if an application only needs read access, don’t grant write permissions.
5. Regularly Update Software
Keep your web application and database management systems up-to-date with the latest security patches.
Is SQL Injection Illegal?
Yes! Performing SQL injection without permission is illegal and considered hacking. Laws vary by country, but in many places, it falls under computer fraud statutes. Just because a vulnerability exists doesn’t give anyone the right to exploit it.
How Can SQL Injection Be Detected?
Detecting SQL injection vulnerabilities involves using various tools and techniques:
- Automated Scanners: Tools like Acunetix or Burp Suite can scan your web application for vulnerabilities.
- Manual Testing: Skilled testers can manually input common attack strings to see if they can manipulate queries.
- Monitoring Logs: Keep an eye on your server logs for unusual activity that might indicate an attempted attack.
Does HTTPS Prevent SQL Injection?
While HTTPS encrypts data transmitted between the user and server, it does not prevent SQL injection attacks. HTTPS protects against eavesdropping but does not safeguard against vulnerabilities in how applications handle user input.
Step-by-Step SQL Injection Attack (For Testing Security)
Important Note
You should only perform these tests on websites you own or have explicit permission to test! Ethical hacking helps identify vulnerabilities so they can be fixed.
Simulating an SQL Injection Attack
Let’s demonstrate how an SQL injection attack works using a testing site specifically designed for this purpose: http://testphp.vulnweb.com/login.php.
Visit the Login Page: Go to this URL.
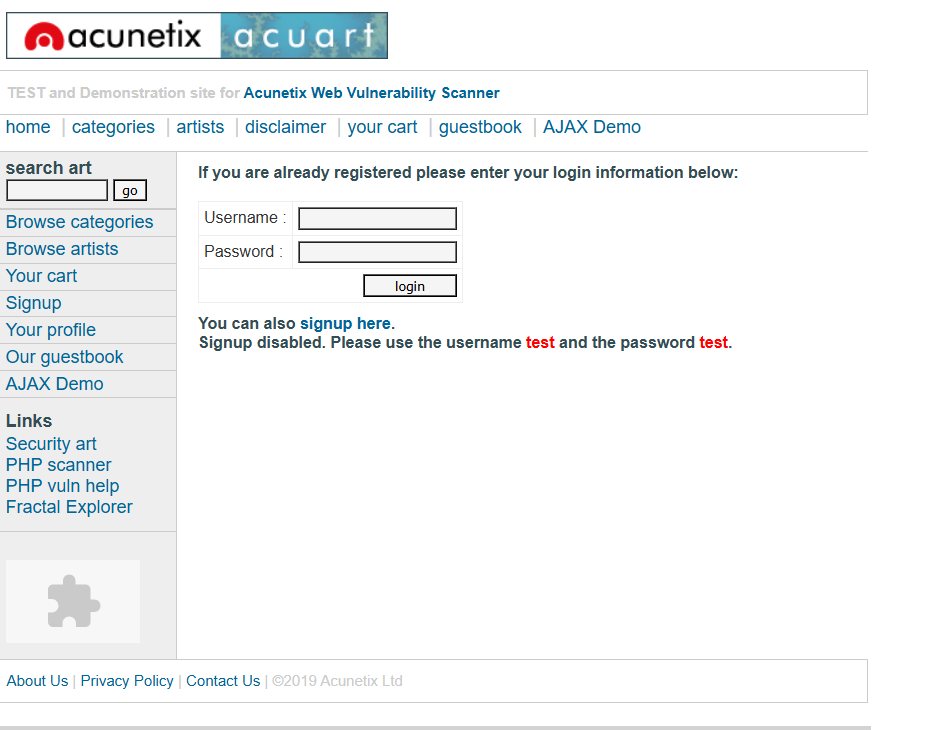
Enter Credentials: Your input should look like this:
-
- For the username field, enter
user1. - For the password field, enter
' OR '1'='1.
- For the username field, enter
-
- Username:
user1 - Password:
' OR '1'='1
- Username:
Submit the Form: Click on the login button.
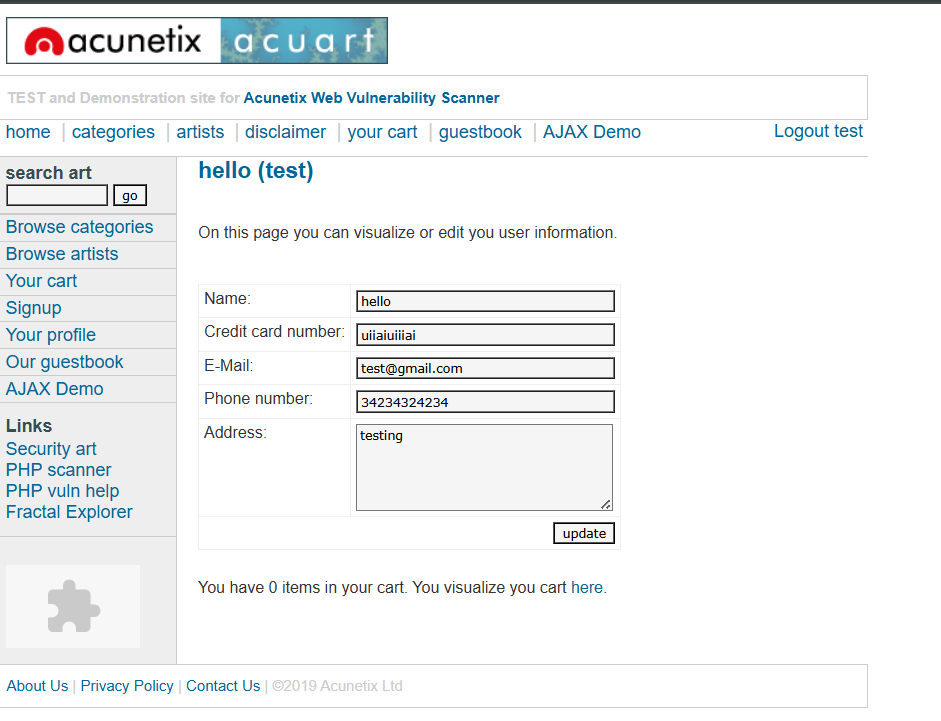
Observe the Outcome: If successful, you will be logged in without needing valid credentials! The underlying query executed by the application would look something like this:
SELECT * FROM users WHERE username = 'user1' AND password = '' OR '1'='1';
This modified query returns true because '1'='1' is always true, allowing access without valid credentials.
Use Tools: Consider using tools like SQLMap for more advanced testing.
Report Findings: If you find vulnerabilities, report them responsibly so they can be addressed.
Responsible Testing
Remember, testing should only be done ethically and legally on sites you own or have permission to test! This process helps identify vulnerabilities so they can be addressed promptly.
Conclusion
SQL injection is a serious threat that can compromise your website’s security if not properly managed. By understanding how it works and implementing preventive measures like parameterized queries and input validation, you can protect your site from potential attacks.
Actionable Checklist for Website Owners
- Use parameterized queries in all database interactions.
- Validate and sanitize all user inputs.
- Implement proper error-handling practices.
- Limit database permissions based on need.
- Regularly update your software and frameworks.
By following these steps, you can significantly reduce the risk of SQL injection attacks on your website!












